Kippo project with kippo-graph
Introduction
This project cover the idea to see how a honey pot works and how a hacker would approach the service he/she is about to hack. The chosen honey pot is a SSH honey pot. This version is called Kippo and is develop by “The honey pot Project”.
The kippo honey pot is a small piece of software running on a small pc or in a KVM environment with maybe 100 or more honey pots covering the IP range of the subnet. In this project is has been chosen to be running on a RPI (Raspberry Pi) on a debian whezzy platform.
The purpose of putting it on a raspberry is that it can be moved around so a problem area can be attended more flexible. There for a startup script was design so when plugged in will would start the service and wait. Kippo-Graph, A service that generate a graphs and tables from the kippo database and presents it on a webpage. But kippo has to look like a up to date system so the Filesystem and information about hardware was updated
The project was being worked at in Viseu, Portugal.
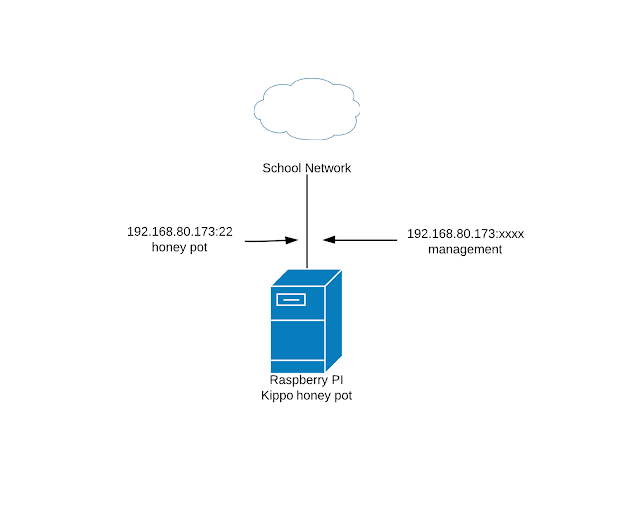
The schools network is presented by the cloud as undefined network with kippo attached to it getting its IP from DHCP somewhere.
Two interfaces are planed:
- One for the attacker
- Two for management
Rules in Iptables had to redirect the traffic from the normal port 22 to the management port. It has be xxxx out purposely so no other then the creator of the honey pot knows it.
Kippo makes:
- Fake filesystem with the ability to add/remove files. A full fake filesystem resembling a Debian 5 installation is included – has to be updated after install
- The possibility of adding fake file contents so the attacker can ‘cat’ files such as /etc/passwd. Only minimal file contents are included
- Session logs stored in an UML compatible format for easy replay with original timing.
- Saves files downloaded with wget for later inspection.
- Trickery; ssh pretends to connect somewhere, exit doesn’t really exit
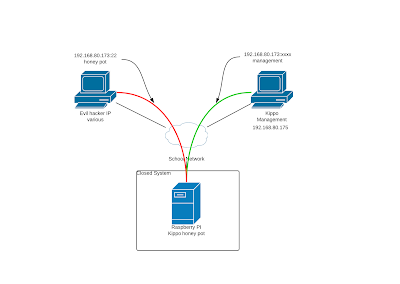
The concept diagram shows how a hacker approaches the system and illustrate that ones he is in he/she is on a closed network and even if the hacker logs out of the system but does close the terminal window.
Using playlog.py is is possible to playback the attack
From the directory /kippo-read-only/log/tty – use following command
~/kippo-read-only/utils/playlog.py <log file name> this will replay the hackers attack
System development
Installed kippo by following the documentation https://code.google.com/p/kippo/
Ran into a problem in the installation that the iptables rule would not save therefore the redirect from port 22 to kippo port would not work and had to be reintroduced upon power failure or reboot, and kippo would not just boot up again. A way to fix this problem had to be fixed somehow. An Idea was to create a boot up script for kippo running in the boot up sequence. But scripts that run there are all run as root user and kippo in no allowed to be run as root.
See details of the script in the program section.
A plan and the idea for a script was written down. Kippo graph was installed following the guide from http://bruteforce.gr/kippo-graph.
This is a web frontend for Kippo to show the most common and most used user/pass used to breach the system. The system was tested by outside client to to see how the kippo would interact with a hacker. Much of the time was then spent to see how to get the kippo to look more real like. To keep the hacker in the honey pot as long as possible. See Updating system section for details
Install kippo
- RaspberryPI model B rev.2
- SD Card – 8GB
- Physical network connection for your RaspberryPI
- A home router/firewall that you can do port forwarding on if it is not directly on the internet
So first off install some of the dependencies to get Kippo running. SSH onto your RaspberryPI and as the pi user run the following command:
sudo apt-get install subversion python-twisted python-mysqldb mysql-server apache2
The mysql-server and apache2 packages are so we can log Kippo to MySQL and run the kippo-graph website.
NOTE: Remember the MySQL password.
So now we need to get a copy of Kippo, we are going to use SVN for this:
svn checkout http://kippo.googlecode.com/svn/trunk/ kippo-read-only
Now the installation will by default download Kippo into /home/pi/kippo.
Need to configure the database now for the kippo-graph.
Log into MySQL:
mysql -h localhost -u root -p
Enter the password password from before and once logged in create a database called kippo:
create database kippo;
And then assign the necessary rights:
GRANT ALL ON kippo.* TO ‘kippo’@’localhost’ IDENTIFIED BY ‘Kippo-DB-pass’;
Now exit from MySQL:
Exit;
Browse to the kippo folder location:
Cd /kippo /doc/sql
Within this folder find a file called mysql.sql this file needs be loaded that into the database:
mysql -u kippo -p
use kippo;
source mysql.sql;
If that worked without errors you should now have a populated database, you can check by typing this within the MySQL prompt:
show tables;
It shall look like this
Exit;
Now it is need to create a kippo.cfg file.
From the root of the /kippo folder type this:
cp kippo.cfg.dst kippo.cfg
This will copy the content kippo.cfg.dst to kippo.cfg
Edit the kippo.cfg file with the database details.
Sudo nano kippo.cfg
Navigate the file and find the [database_mysql] section, un-comment all the fields, including the [database_mysql] and modify the values so it looks something like this:
[database_mysql]
host = localhost
database = kippo
username = kippo
password = Kippo-DB-pas
Kippo uses port 2222 to run its honeypot on, in order to send hackers to that port it is needed if there is a router in front of the kippo to port forward all traffic for port 22 to 2222.
If honeypot directly on the internet following additional steps is needed:
- sudo apt-get install iptables
- sudo iptables -t nat -A PREROUTING -p tcp –dport 22 -j REDIRECT –to-port 2222
- sudo iptables-save > /etc/iptables.rules
Change the default port of the ssh server a higher port. Use this command to change the listening port for the sshd to 65534:
sudo sed -i ‘s:Port 22:Port 65534:g’ /etc/ssh/sshd_config
Restart your ssh service
sudo /etc/init.d/ssh restart
Login again with ssh ‘user’@ip –p 65534-. Navigate to /kippo run following command to start the honeypot
sudo ./start.sh
Check it’s loaded properly by looking in the /kippo /log/kippo.log file which should show it starting up properly and you can then run this command to check:
sudo netstat -antp | grep 2222
Which should return an entry saying port 2222 is listening a python process is running.
The root password for the Kippo honeypot is ‘123456‘ it can be change by editing the /kippo /data/userdb.txt file and restarting kippo.
Installing the kippo-graph
Install dependencies
- sudo apt-get install libapache2-mod-php5 php5-cli php5-common php5-cgi php5-mysql php5-gd
- sudo /etc/init.d/apache2 restart
Navigate to /var/www and tun following commands
- wget http://bruteforce.gr/wp-content/uploads/kippo-graph-0.9.tar
- sudo tar xvf kippo-graph-0.9.tar –no-same-permissions
cd kippo-graph - sudo chmod 777 generated-graphs
Before opening the website the /var/www/config.php file with the database properties from earlier has to be configured so it looks like this:
Now go to the website
http://<raspberrypi_ipaddress>/kippo-graph/index.php
Updating the system
Boot up sequence
The script made for rebooting .
Kippo can´t run as root. Every script that boots up in the boot sequence is run as root. There for another way for normal doing the scripts just by adding the path and the script to the rc.local file fails.
su -c /home/pi/kippo.sh pi &
This line of code in the rc.local file change user to pi and then calls the desired script
This small script sets up a iptable rule that redirect all traffic to port 22 to port 2222
The by telling where the directory of the file that has to be executed are and the start.sh to run kippo this start the kippo to run in the background. But if the creator or analyst wants to observe the attack real-time this command from the kippo directory will launch kippo to be viewed as the magic happens
FS update
utils/createfs.py > fs.pickle
This takes a copy of the existing file system without any security compromising issues.
New base file added to give a more real look for a hacker
URL https://gist.github.com/zwned/5588521
This python script from Gist will populate some of the environment variables like uptime and Top command.
Added commands from github rep https://github.com/basilfx/kippo-extra
Another Github repository this is from Basilfx updating environmental variables
/usr/bin/env – current environment variables
/usr/bin/gcc – fake compiler with file output
/sbin/iptables – fake firewall management, supports flush and list for different tables /chains
/bin/which – path of binary
These are updates that takes info from running system kippo is on.
cat /proc/cpuinfo > /home/user/kippo/honeyfs/proc/cpuinfo
cat /etc/issue > kippo/honeyfs/etc/issue
cat /etc/passwd > kippo/honeyfs/etc/passwd – Changing cpu info to the system it is running on.
Update txtcmds:
dmesg > kippo/txtcmds/bin/dmesg
mount > kippo/txtcmds/bin/mount
how long can a hacker enter it?
Security wise there have been none implementet but is only a working example nothing more. Security could be added by hardning x-pack from elastic, switch to https make it only read-only, hide it behind a proxy and implementing security recomendations for apache and the OS