SSH Key Authentication with LDAP
Server configuration
I’m running Gosa as a webUi. A desent tool that unfortunate is beginning to be old and missing updates. I’m not sure at the moment if the project is alive or we have seen the last of the Gosa UI
To get started, install the gosa-plugin-ssh gosa-plugin-ssh-schema to add this to the configuration of gosa. Next restart the apache server for it to take effect in the WebUi.
If you are not using Gosa then make a *.ldif file and add the content of the openssh-lpk.ldif file but leave the content from the “entryUUID” and below.
I had a problem adding a key to gosa. It need to have the right format and e.g putty dont give you that so. But if the following syntax is kept it should accecpt the key.
Gosa public key syntax: ssh-rsa <key> “comment” user@hostname
But don’t at your public key the gosa add key function. It will hash it and at the moment I don’t know how to undo the hash to get my key.
Firstly, check that the schema is present and it looks like this at location
/etc/ldap/slapd.d/cn\=config/cn\=schema/cn\=\{0\}openssh-lpk.ldif
# AUTO-GENERATED FILE – DO NOT EDIT!! Use ldapmodify.
# CRC32 2619b35e
dn: cn=openssh-lpk
objectClass: olcSchemaConfig
cn: {0}openssh-lpk
olcAttributeTypes: ( 1.3.6.1.4.1.24552.500.1.1.1.13 NAME ‘sshPublicKey’ DESC ‘MANDATORY: OpenSSH Public key’ EQUALITY octetStringMatch SYNTAX 1.3.6.1.4.
1.1466.115.121.1.40 )
olcObjectClasses: ( 1.3.6.1.4.1.24552.500.1.1.2.0 NAME ‘ldapPublicKey’ DESC ‘MANDATORY: OpenSSH LPK objectclass’ SUP top AUXILIARY MAY ( sshPublicKey $
uid ) )
structuralObjectClass: olcSchemaConfig
entryUUID: fef23996-8c64-1034-8985-2950d6358a31
creatorsName: cn=config
createTimestamp: 20150511200646Z
entryCSN: 20150511200646.585107Z#000000#000#000000
modifiersName: cn=config
modifyTimestamp: 20150511200646Z
Secondly check for existent key by doing
ldapsearch -x ‘(&(objectClass=posixAccount)(uid='<Your user>’))’ sshPublickey
Then I can see if my user has a key specified and If you have added it with gosa it will probably say something like
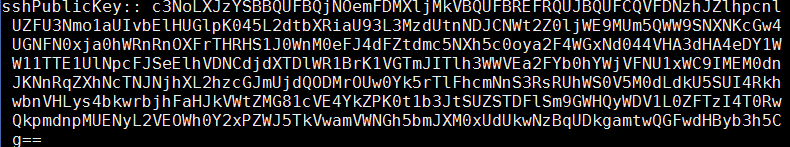
sshPublicKey::c3NoLXJzYSBBQUFBQ…….. bla bla
This is because it is getting hashed in someway that I haven’t figured out yet but you can do this manually with creating a file called e.g sshkey.ldif and add the following content.
dn: cn=Jonas Pedersen,ou=people,dc=kirk,dc=local
changetype: modify
add: objectClass
objectClass: ldapPublicKey
–
add: sshPublicKey
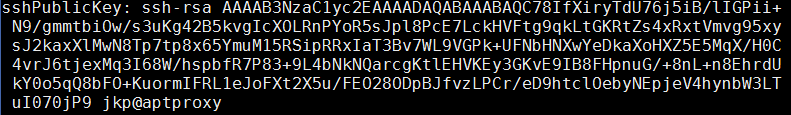
sshPublicKey: ssh-rsa <your_key> “Comment” jkp@aptproxy
Before modifying log in and delete the key from the gosa webui and ldapsearch for it again to check it is not present and create a *.ldif file and add following. Note: dn is used to define the user that we are about to modify.
Then modify it with ldapmodify
ldapmodify -x -D cn=admin,dc=kirk,dc=local -W -f sshkey.ldif
Then do a control to see if the output iss in a public key syntax.
ldapsearch -x ‘(&(objectClass=posixAccount)(uid='<Your user>’))’ sshPublickey
Client configuration setup
Make sure the Version of openSSH is >6.2. This can be archived either by upgrading to Debian 8 by changing the source.list file with Jessie instead of Wheezy like
deb http://apt-proxy:3142/debian/ wheezy main
deb-src http://apt-proxy:3142/debian/ wheezy main
To
deb http://apt-proxy:3142/debian/ jessie main
deb-src http://apt-proxy:3142/debian/ jessie main
Then do
apt-get update && apt-get dist-upgrade
This will take some time. But upgrading the dist is one the best features Debian has. It is not locked in anyway to a specific distribution or version.
But always test the upgrade on a test server before moving it into production.
Other option than upgrading is to download the source file and compile it.
Need some dependencies for that so “apt-get install build-essential”
Then run following commands
- wget ftp://mirror.one.com/pub/OpenBSD/OpenSSH/portable/openssh-6.8p1.tar.gz
- tar -zxvf openssh-*.tar.gz
- cd openssh-6.8p1
- ./configure –with-md5-passwords –sbindir=/usr/sbin –with-pam
- make
- make install
Client Configurations
We are adding a script to look up a public key. First the configuration of the sshd_config file.
nano /etc/ssh/sshd_config
Under the AuthorizedKeysFile line add following
AuthorizedKeysCommand /etc/ldap/sshLDAPkey.sh
AuthorizedKeysCommandUser sysk
The first line is the path to the ssh ldap script used to fetch key from ldap user. Second line is the user that runs the script.
sshd_config man page
AuthorizedKeysCommand
Specifies a program to be used to look up the user’s public keys.
The program must be owned by root and not writable by group or others. It will be invoked with a single argument of the username
being authenticated, and should produce on standard output zero or
more lines of authorized_keys output (see AUTHORIZED_KEYS in sshd(8)). If a key supplied by AuthorizedKeysCommand does not successfully authenticate and authorize the user then public key authentication continues using the usual AuthorizedKeysFile files. By default, no AuthorizedKeysCommand is run.
AuthorizedKeysCommandUser
Specifies the user under whose account the AuthorizedKeysCommand is run. It is recommended to use a dedicated user that has no other role on the host than running authorized keys commands.
Restart the service
/etc/init.d/ssh restart
In Debian Jessie the status looks a bit different than it used to. E.g in wheezy it reported failed or running. But with Systemd I have experienced that even if it restarts the service it actually can fail without knowing it. Therefore do a /etc/init.d/ssh status to be sure.
Make a script in a desired location. A good spot could be in the specified users home folder so none without sudo privileges cant see or edit the script in any way.
nano /home/sysk/sshLDAPkey.sh
Add
ldapsearch -x ‘(&(objectClass=posixAccount)(uid='”$1″‘))’ ‘sshPublicKey’ | sed -n ‘/^ /{H;d};/sshPublicKey:/x;$g;s/\n *//g;s/sshPublicKey: //gp
chmod 755 /etc/ldap/sshLDAPkey.sh
As man page says it may not be
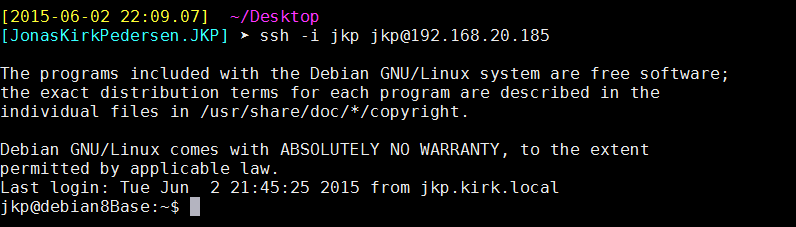
Now test the connectivity with ssh key
All working great.
Send me a comment if you run into trouble.