Basic Management Of LDAP Users
Introduction
See installation of LDAP server
Starting using with the only command line tool available is a bit scary. But I think it will be fun and interesting to learn before installation a web interface to mange the ldap service. Because I dont think in any way that I can escape it for long.
There are 3 commands that I need to get my head into.
- ldapadd
- ldapsearch
- ldapmodify
In this post I will scratch the surface of ldapadd and ldapsearch.
Starts with the file name options
ldapadd [OPTIONS] [CREDENTIALS] filename
With a *.ldif file I can add all my users to and populate the ldap database with system users .
Users and Groups
Starting by adding two new OU’s – Users and Groups.
Create a ldif file named ‘ou.ldif’ with this info in the file:
nano /etc/ldap/ou.ldif
dn: ou=Groups,dc=kirk
ou: Groups
objectClass: top
objectClass: organizationalUnitdn: ou=Users,dc=kirk
ou: Users
objectClass: top
objectClass: organizationalUnit
Using the ldapadd command to add the two new OU (Organizational Unit)
ldapadd -x -D cn=admin,dc=kirk -W -f ou.ldif
Result
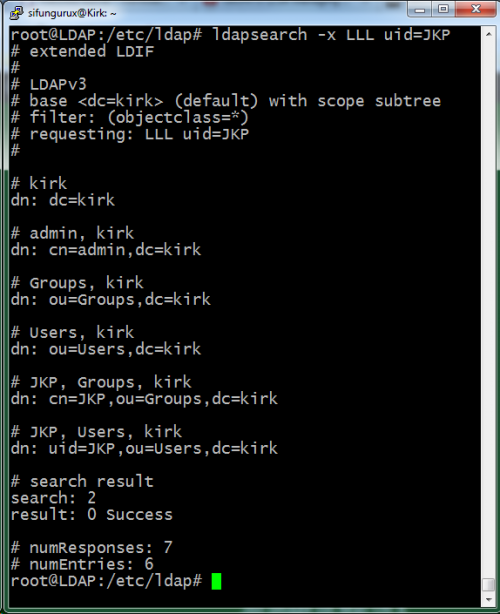
adding new entry “ou=Groups,dc=kirk”
adding new entry “ou=Users,dc=kirk”
Added me as a user in this users.ldif file
nano /etc/ldap/users.ldif
dn: cn=JKP,ou=Groups,dc=kirk
cn: JKP
gidNumber: 5000
objectClass: posixGroupdn: uid=JKP,ou=Users,dc=kirk
uid: JKP
uidNumber: 5000
gidNumber: 5000
cn: Jonas Pedersen
sn: Pedersen
objectClass: posixAccount
objectclass: organizationalPerson
loginShell: /bin/bash
homeDirectory: /home/JKP
Where
- uid = username
- cn = common name
- sn = surname
This is a simple user entry. Nothing much in this one.
ldapadd -x -D cn=admin,dc=kirk -W -f users.ldif
adding new entry “cn=JKP,ou=Groups,dc=kirk”
adding new entry “uid=JKP,ou=Users,dc=kirk”
and file test that is has been added to the ldap server correcly
Adding a client to the mix
I had a bit of trouble getting this working correctly and the reason is most guides and info are Pre 2014 where the structure of the ldap service changed.
But I will try lay out how I solved my issues
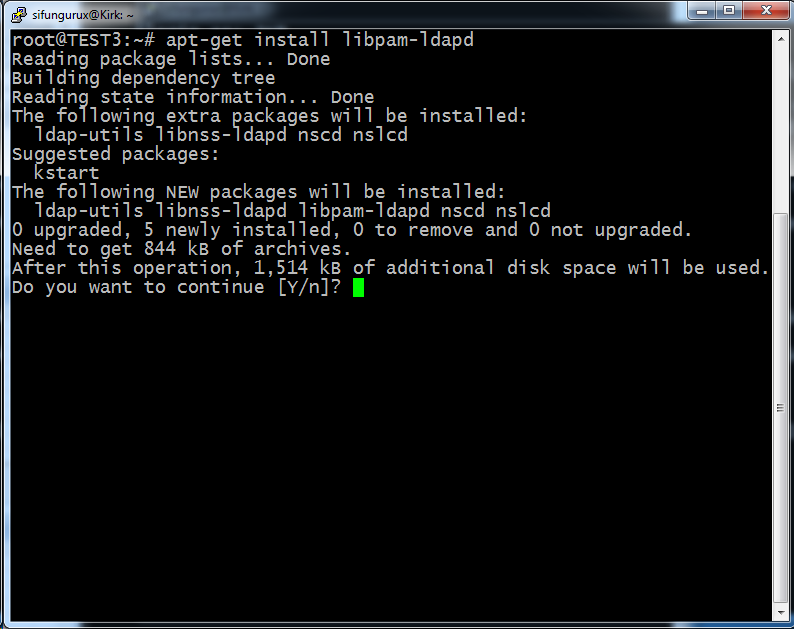
apt-get install -y libpam-ldapd
And it will install following packages
- libnss-ldapd
- nscd
- nslcd
For user connectivity it is not necessary to configure anything else than libpam-ldapd when it is installed.
After install have started I got prompt from 3 questions
- Ldap server address
- Distinguished Name
- And services to configure
The configuration I have made here is simple and only to get a feeling of how ldap works. There is a lot of aspekst that are missing, like security and encryption of the connection between client and server.
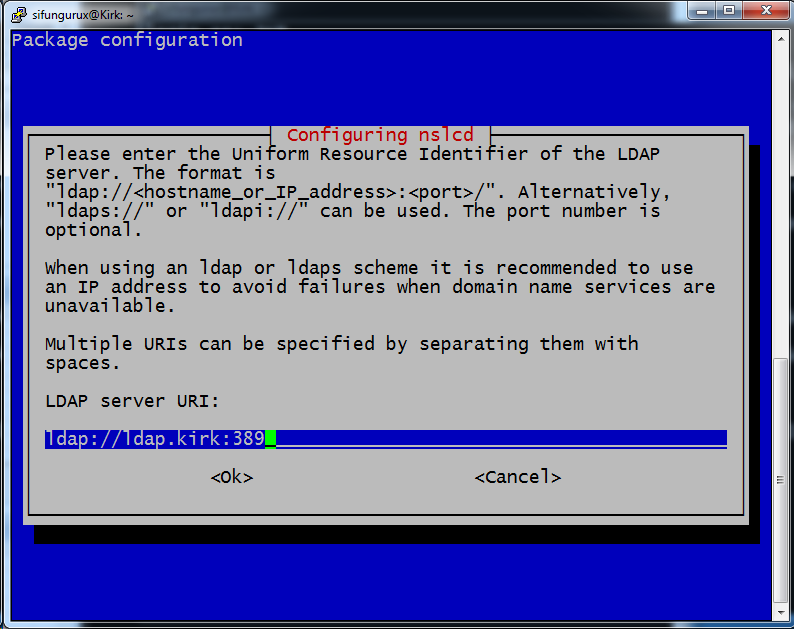 If you have a working environment with supported dns then it is best practices to use the hostname instead of an IP address, but in this case the setup instruction might be right. Then the possibility is to add two URI´s to the configuration, Like I did here and then add a second one with the IP address.
If you have a working environment with supported dns then it is best practices to use the hostname instead of an IP address, but in this case the setup instruction might be right. Then the possibility is to add two URI´s to the configuration, Like I did here and then add a second one with the IP address.
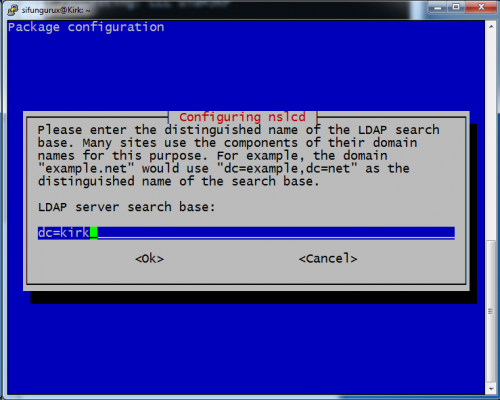 My domain is *.kirk so I will add dc(domain container)=kirk.
My domain is *.kirk so I will add dc(domain container)=kirk.
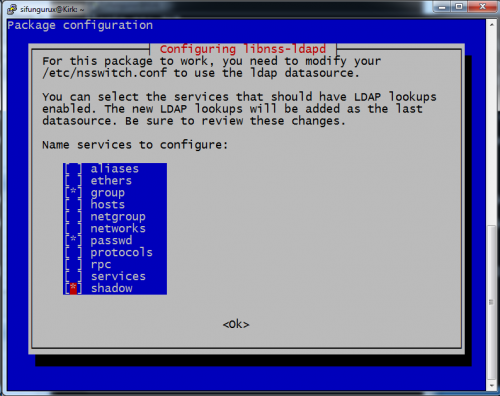 Last thing is to choose what services ldap should support. Here I have chosen group, passwd and shadow. Press OK and the installation will end and services will restart and now it is possible to log in with the ldap user/Pass
Last thing is to choose what services ldap should support. Here I have chosen group, passwd and shadow. Press OK and the installation will end and services will restart and now it is possible to log in with the ldap user/Pass
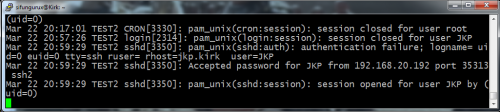
And a quick test shows it
First picture is the login screen and the second one is a of
tail -f /var/log/auth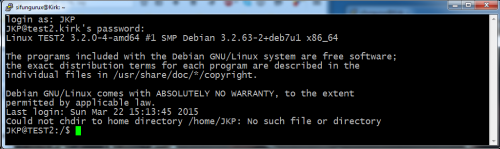
One thought on “Basic Management Of LDAP Users”